CSPs are typically challenged to meet the requirements of a diverse client
base. To build a sustainable model, it is essential that the CSP establish
a strong foundation of controls that can be applied to all of its clients.
In that regard, the CSP can use the concept of GRC that has been adopted
by a number of leading traditional outsourced service providers and CSPs. GRC recognizes that compliance is not a point-in-time
activity, but rather is an ongoing process that requires a formal
compliance program. Figure 1 depicts such a
programmatic approach to compliance.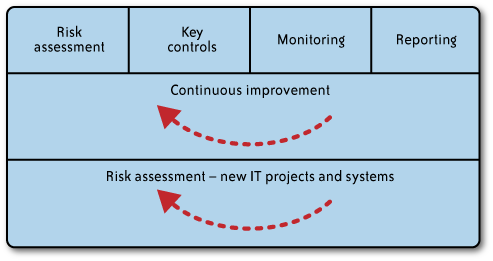
Key components of this approach include:
Risk assessment
This approach begins with an assessment of the risks that face
the CSP and identification of the specific compliance
regimes/requirements that are applicable to the CSP’s services. The
CSP should address risks associated with key areas such as
appropriate user authentication mechanisms for accessing the cloud,
encryption of sensitive data and associated key management controls,
logical separation of customers’ data, and CSP administrative
access.
Key controls
Key controls are then identified and documented to address the
identified risks and compliance requirements. These key controls are
captured in a unified control set that is designed to meet the
requirements of the CSP’s customers and other external requirements.
The CSP drives compliance activities based on its key controls
rather than disparate sets of externally generated compliance
requirements.
Monitoring
Monitoring and testing processes are defined and executed on an
ongoing basis for key controls. Gaps requiring remediation are
identified with remediation progress tracked.
The results of ongoing monitoring activities may also be used
to support any required external audits.
Reporting
Metrics and key performance indicators (KPIs) are defined and reported on an ongoing basis. Reports
of control effectiveness and trending are made available to CSP
management and external customers, as appropriate.
Continuous improvement
Management improves its controls over time—acting swiftly to
address any significant gaps identified during the course of
monitoring and taking advantage of opportunities to improve
processes and controls.
Risk assessment—new IT projects and systems
The CSP performs a risk assessment as new IT projects, systems, and services are developed to
identify new risks and requirements, to assess the impact on the
CSP’s current controls, and to determine whether additional or
modified controls and monitoring processes are needed.
The CSP also performs an assessment when considering entry
into a new industry or market or taking on a major new client with
unique control requirements.
1. Benefits of GRC for CSPs
CSPs must adhere to a variety of IT process control requirements including
external requirements and internal requirements. As we examine these
requirements, we find numerous points of intersection. By combining
compliance efforts to address all of these requirements and taking a
more uniform and strategic approach, increased efficiencies and
compliance can be attained. Instead of performing control review and
testing cycles separately, control language and testing can be
structured to address the needs of multiple sets of requirements.
Therefore, control review and testing need to be completed only once to
meet the demands of multiple sets of requirements. This strategic
approach results in a decreased level of effort to meet control
requirements and increased compliance due to the control language being
defined in a more efficient manner to support many compliance
needs.
CSPs often struggle to meet the many demands of compliance
requirements. These efforts are often in silos, unstructured, and
reactive in nature. Repeatedly non-compliant controls are discovered
during the course of an audit or as a result of a security incident. By
implementing a structured compliance program and organization,
significant benefits can be derived.
Achieving periodic silos of compliance mostly as a result of
third-party reviews will be replaced by an ongoing focus on compliance
to increase overall IT process compliance in a more efficient
manner.
The use of KPIs and compliance-based risk assessments will provide
valuable insight into areas of IT control weaknesses. Improved
visibility into IT control weaknesses can greatly enhance decision
making for new investments, placing precious resources where there is
the greatest need.
Continuous controls monitoring will be performed to shift from a detective approach
discovering compliance failures to a more preventive approach of
regularly reviewing control effectiveness and thereby avoiding
compliance failures before they can occur.
With proactive compliance management performed by control and
compliance subject matter professionals, control changes required
through the introduction of new regulations, threats, and IT systems can
be more smoothly managed and integrated into the control
environment.
Compliance benefits can be further extended by more effectively
using automation to improve control compliance.
In summary, a GRC approach helps a CSP to:
Reduce risks through a structured risk management
approach
Improve monitoring of IT compliance
Improve security
Rationalize compliance requirements and control assessment
processes
Reduce the burden of compliance monitoring and testing
2. GRC Program Implementation
To implement a GRC program several major scope elements must be developed,
approved, and put in place. The major components of work have been
broken down into the following work streams: governance, risk
management, compliance, and continuous improvement. Figure 2 depicts a typical process for
implementing a unified IT compliance program.
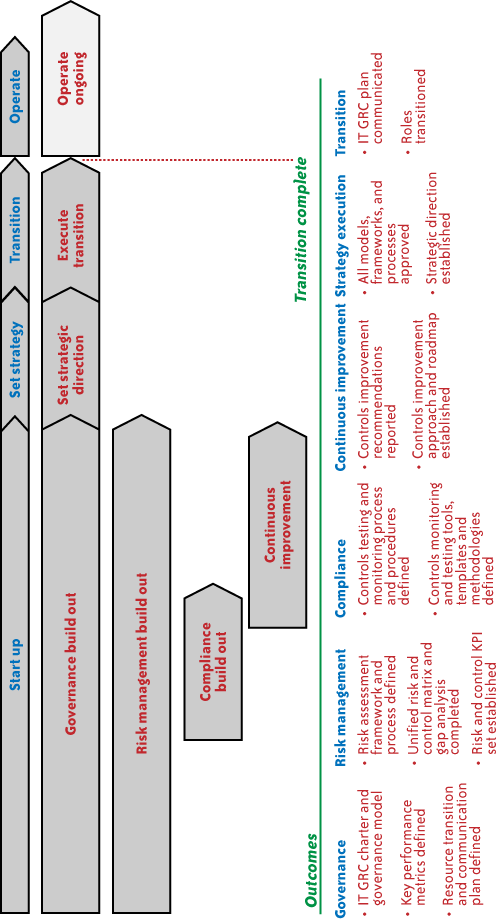
Start-up involves building out all the major work components
necessary to define and operate the program. This is generally led and
performed by the GRC team working with guidance and input from
IT management. This will include the following:
Governance build-out
The operating scope/charter, procedures, and governance
mechanisms for the GRC team will be developed.
An organizational change management and transition plan
will be developed to assist the organization in communicating
how the GRC team will integrate with the CSP as a
whole.
Risk management build-out
A risk assessment framework will be developed leveraging
existing methodologies. This framework will be tailored to the
CSP’s processes and will be accompanied by a risk assessment
process definition.
The CSP’s compliance requirements will be rationalized
to support the development of the unified control
matrix.
The unified control matrix will be developed and mapped
against current control processes with gaps identified.
KPIs will be defined to monitor progress and provide a basis
for ongoing measurement and project management office
dashboard reporting.
Compliance build-out
The testing/monitoring processes and procedures, tools,
templates, and methodologies will be developed to support
effective compliance utilizing a standardized and efficient
approach.
Continuous improvement
Controls improvement recommendations will be developed, risk-rated, and
prioritized.
Set strategy
The set-strategy phase will encompass the GRC team
presenting the program as a whole to the GRC oversight group and
acquiring consensus and approval for the program strategy and
approach.
Transition
The transition phase will comprise a short period of
communicating the new GRC roles and introducing resources and
activities to the broader organization.
Operate
The operate phase is when the ongoing services are made
operational and the program executes its charter, strategy, and
approach as defined and approved in previous phases.